Introduction:
In the realm of secure communication and system administration, SSH (Secure Shell) has emerged as a cornerstone technology. Central to the secure authentication process in SSH is the use of cryptographic keys. SSH key pairs, consisting of a private key and a corresponding public key, provide a robust and secure method for authenticating users and ensuring the integrity and confidentiality of data transfers. In this comprehensive guide, we will delve into the intricacies of SSH key generation, covering the fundamentals, the key types, the generation process, best practices, and advanced usage scenarios.
SSH keys are asymmetric, meaning they consist of a pair of keys: a private key and a public key. The private key is kept secure on the user's device, while the public key can be shared and placed on remote servers.
SSH supports various key types, with RSA and Ed25519 being the most commonly used. RSA, named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman, has been a standard for a long time. Ed25519, based on elliptic curve cryptography, is gaining popularity for its strong security properties and efficiency.
The strength of an SSH key is measured in bits. The larger the key size, the more secure the key is against brute-force attacks. Common key sizes include 2048, 3072, and 4096 bits.
OpenSSH is the most widely used implementation of SSH. To generate an SSH key pair, the ssh-keygen utility is utilized. The basic syntax is as follows:
ssh-keygen -t <key_type> -b <key_size> -f <output_filename>
Example:
ssh-keygen -t rsa -b 2048 -f ~/.ssh/id_rsa
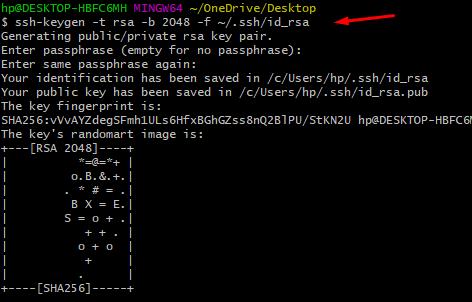
This command generates an RSA key pair with a key size of 2048 bits and saves it to the ~/.ssh directory with the filenames id_rsa for the private key and id_rsa.pub for the public key.
Running ssh-keygen without any options will prompt an interactive configuration, allowing users to customize parameters such as key type, key size, and output filename.
ssh-keygen
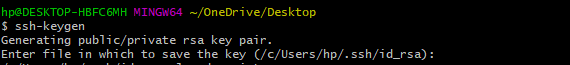
Users have the option to add an extra layer of security by adding a passphrase to the private key. This passphrase acts as a password and must be entered each time the private key is used.
Choose a key size and type that aligns with current security standards. As of now, a key size of 2048 bits is considered the minimum, while 3072 or 4096 bits provide higher security.
ssh-keygen -t rsa -b 4096 -f ~/.ssh/id_rsa_secure
Generate a unique key pair for each device to avoid a compromise on one device affecting the security of other devices.
Regularly rotate and update SSH keys to enhance security. This practice limits the window of vulnerability in case a private key is compromised.
Consider using passphrases for added security. Even if the private key is compromised, an attacker would still need the passphrase to use it.
Safeguard private keys by storing them in secure locations. Use password protection for key storage, and avoid sharing private keys.
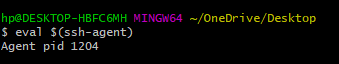
The SSH agent is a key management tool that allows users to add their private keys to a single agent process, eliminating the need to re-enter passphrases for each use. Start the SSH agent:
eval $(ssh-agent)
Add a private key:
ssh -A user@remote-server
SSH certificates, issued by a certificate authority, provide an additional layer of security and control. Certificates allow for centralized management and control over user access.
In the event of a compromised key, key revocation becomes crucial. Remove compromised keys from authorized key files on servers and regenerate new key pairs.
Automated tools and scripts can be employed for key rotation, ensuring that the process is streamlined and consistently applied across multiple devices.
Ensure that the private key has the correct permissions. Private keys should only be readable and writable by the owner.
chmod 600 ~/.ssh/id_rsa
Verify that the key is in the correct format. RSA keys, for example, should start with -----BEGIN RSA PRIVATE KEY-----.
If using a passphrase-protected key, ensure that the correct passphrase is entered. Consider using the ssh-add command to avoid repeated passphrase prompts.
Confirm that the public key is correctly added to the ~/.ssh/authorized_keys file on the remote server.
If encountering key mismatch issues, ensure that the private key matches the public key added to the server's authorized keys file.
SSH key generation is a fundamental skill for anyone involved in system administration, DevOps, or secure communication. Understanding the basics, mastering the key generation process, and implementing best practices are essential for maintaining a secure and efficient workflow.
As technology advances and security threats evolve, the importance of robust authentication mechanisms cannot be overstated. SSH keys, with their cryptographic strength and versatile usage scenarios, play a pivotal role in securing remote connections and data transfers.
By adhering to best practices, regularly updating keys, and leveraging advanced features such as SSH agents and key forwarding, administrators can fortify their systems against unauthorized access and potential security breaches. Whether used for individual devices or integrated into a broader security infrastructure with certificate authorities, SSH keys remain a cornerstone of secure communication in the digital age.