In the ever-evolving landscape of online security, the use of SSL/TLS certificates has become a fundamental practice to ensure secure communication between users and web servers. Certificate Authorities (CAs) play a pivotal role in issuing SSL certificates, and one crucial step in the validation process involves DNS CNAME validation. In this comprehensive guide, we will explore the significance of DNS CNAME validation for SSL certificates, the validation process, and how it contributes to a more secure online environment.
SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security), are cryptographic protocols that secure the communication between a user's web browser and a website's server. SSL/TLS certificates, issued by trusted CAs, validate the identity of a website, encrypt data in transit, and establish a secure connection. This is particularly crucial for protecting sensitive information such as login credentials, personal details, and financial transactions.
SSL certificates are categorized into different types based on the level of validation they undergo. Domain Validation (DV) certificates, Organization Validation (OV) certificates, and Extended Validation (EV) certificates represent increasing levels of scrutiny and verification of the entity requesting the certificate.
DNS (Domain Name System) CNAME validation is a specific method employed by CAs to verify the ownership of a domain during the SSL certificate issuance process. This validation mechanism adds an extra layer of assurance that the entity requesting the certificate has control over the domain for which the certificate is being issued.
Certificate Request: When an entity applies for an SSL certificate, the CA generates a unique token or key pair that needs to be added to the DNS records of the domain.
Token Placement: The entity is required to create a CNAME (Canonical Name) record in the DNS configuration of the domain, pointing to the CA's validation server and including the unique token or key pair.
CA Verification: The CA then queries the DNS records for the specified domain, looking for the CNAME record with the correct token. If the record is found, the CA validates that the entity has control over the domain.
Certificate Issuance: Upon successful validation, the CA issues the SSL certificate for the specified domain.
DNS CNAME validation is often automated and can be completed swiftly, reducing the time required for the SSL certificate issuance process. This automation enhances efficiency for both certificate authorities and the entities seeking SSL certificates.
By requiring modifications to DNS records, DNS CNAME validation ensures that the entity requesting the SSL certificate has control over the domain's DNS settings. This adds an extra layer of security, making it more challenging for malicious actors to fraudulently obtain SSL certificates for domains they do not own.
Automation in DNS CNAME validation minimizes the chances of human error during the validation process. This is crucial for maintaining the integrity and security of SSL certificate issuance.
The automated nature of DNS CNAME validation makes it scalable, allowing CAs to efficiently handle a large volume of certificate requests. This is particularly beneficial in the context of the growing demand for SSL certificates as more websites prioritize security.
Let's explore the typical steps involved in performing DNS CNAME validation for SSL certificates:
The entity applies for an SSL certificate and provides the necessary information, including the domain for which the certificate is requested.
The CA generates a unique token or key pair that will be used for validation.
The entity accesses the DNS configuration for the specified domain and creates a CNAME record pointing to the CA's validation server. The CNAME record includes the unique token generated by the CA.
Example CNAME Record:
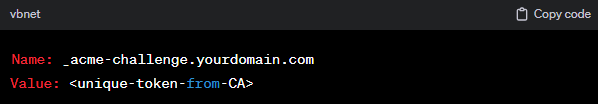
The entity updates the DNS records for the domain with the newly created CNAME record.
The CA queries the DNS records for the specified domain, looking for the CNAME record with the correct token. If the record is found, the CA validates that the entity has control over the domain.
Upon successful validation, the CA issues the SSL certificate for the specified domain.
While DNS CNAME validation provides robust security and automation benefits, certain challenges and best practices should be considered:
The Time-to-Live value in DNS records determines how long the records can be cached. It's advisable to set a reasonably short TTL during the validation process to ensure that changes take effect promptly.
To streamline the DNS CNAME validation process, consider using automated DNS configuration tools or scripts. This helps minimize manual errors and ensures consistency in the configuration across different environments.
The unique token generated by the CA is a sensitive piece of information. It's crucial to handle and store this token securely to prevent unauthorized access and potential misuse.
Implement monitoring systems to track changes in DNS records. Any unexpected or unauthorized modifications to DNS settings should be promptly identified and investigated.
Ensure that personnel involved in the SSL certificate issuance process are well-trained on the procedures, and maintain comprehensive documentation to support the process.
DNS CNAME validation is a critical step in the SSL certificate issuance process, providing an additional layer of security and efficiency. By verifying domain ownership through modifications to DNS records, CAs can ensure that SSL certificates are issued to legitimate entities with control over the specified domains.
As the digital landscape continues to evolve, the importance of secure communication cannot be overstated. DNS CNAME validation, as part of the SSL certificate issuance process, contributes significantly to the overall security posture of websites and online services. System administrators, web developers, and IT professionals should be well-versed in the intricacies of DNS CNAME validation to enhance the security of their online infrastructure and protect users' sensitive information.